- Your cart is empty
- Continuar comprando
What Is Payroll Fraud? Payroll Fraud Investigation Financial Crime
It’s a very real, very costly problem affecting businesses of all sizes. In fact, studies show that payroll fraud occurs in roughly 27% of all businesses, with small to mid-sized companies hit the hardest. Any attempt to manipulate contract information can lead to significant legal risks and penalties for the employer, including fines and litigation costs. Employers found guilty of such practices may face penalties from the labor authorities and potential lawsuits from affected employees, which can result in costly settlements and damage to the company’s reputation.
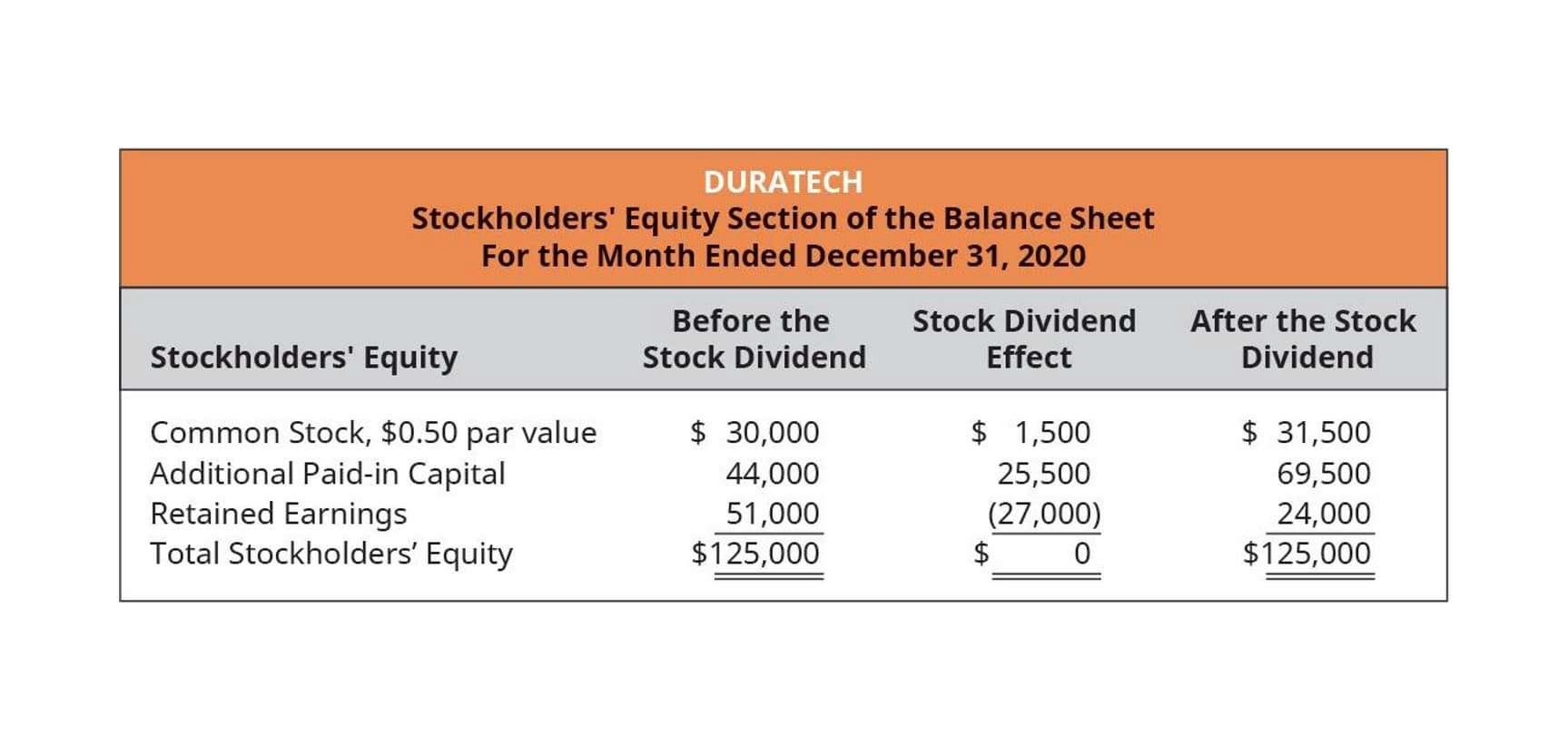
Fraudulent Claims Over Number of Units Produced

Before hiring new employees, especially those who will handle payroll or sensitive financial information, conduct thorough background checks. Look for any red flags such as prior incidents of fraud, financial instability, or discrepancies in their employment history. An example of this would be if a manager were to mark another employee’s earnings as going into a Roth IRA, but in reality, they were just funneling the money into payroll their own private bank account. Fraud of this nature would result in a criminal charge of embezzlement as well as a violation of state laws relating to wages and fringe benefits. While technology has made payroll fraud easier in some ways, technology may also be used to prevent fraud.
- Even when a company has insurance, they’ll eventually pay for this as well, through increased premiums in the future.
- An employee uses a company expense account for personal expenses, then submits them as business-related.
- For example, if commissions are paid on sales and not adjusted for credits, sales with subsequent credits may start appearing.
- DOJ may pursue criminal cases against individuals and entities it believes are promoting false ERC claims.
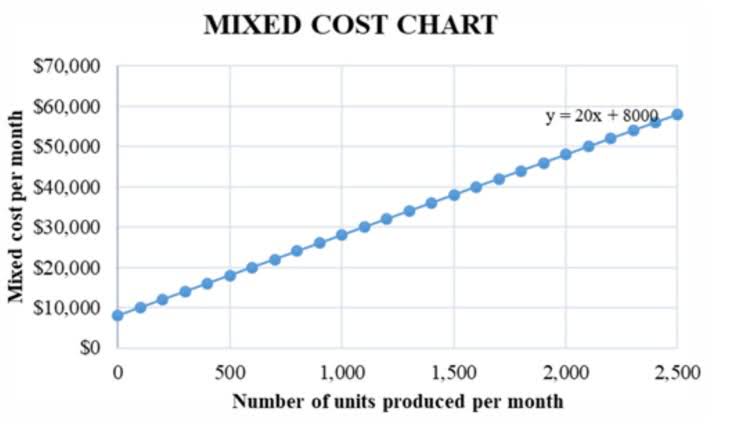
Some Basic Controls
For example, let’s say there is a payroll clerk by the name of John Doe. John has decided that he wants more money from work, so he makes a “new” employee named John Doe-Lynn. So then, when he runs payroll, he can create and issue two checks, one legitimate to John Doe, and then another to John Doe-Lynn. Those actors used messaging applications such as Telegram to provide instructions for completing online forms without triggering anti-fraud software and exchange stolen PII. Some of the stolen PII was obtained via cyberattacks against companies that maintain PII databases, including Experian, Yahoo, LinkedIn, and Facebook. Some states have laws and ethical rules regarding solicitation and advertisement practices by attorneys and/or other professionals.
Louisiana Issues Guidance on Use Tax on Vehicles Registered by New Residents

By fostering a culture of integrity, organizations can reduce the likelihood of fraudulent behavior. Payroll fraud schemes are among the most damaging to a company because they tend to take place over a long period of time. According to the Association of Fraud Examiners (ACFE) the median duration between the start of a payroll fraud scheme and its detection is 24 months — enough time to do some significant financial damage to a company. And some experts estimate that almost a quarter of businesses are affected by payroll fraud each year.
Ghost employee fraud
The process often begins with a comprehensive review of payroll records, including employee files, timekeeping systems, and bank statements. Forensic accountants use advanced analytical tools to sift through vast amounts of data, identifying inconsistencies and irregularities that may have gone unnoticed. Techniques such as data mining and statistical analysis can Online Bookkeeping reveal hidden relationships and trends, making it easier to pinpoint fraudulent activities. For example, they might uncover a pattern of payments to non-existent employees or detect unusual spikes in payroll expenses that do not align with business operations.
What strategies can employers implement to mitigate the risk of payroll fraud? To effectively employer payroll frauds combat payroll fraud, employers should prioritize employee training and implement robust internal audits. Comprehensive training programs educate employees about the consequences of payroll fraud and promote ethical practices within the workplace.
Paycheck Theft
When employees or leadership lose faith in the system, it can affect morale and even your company culture. Keep diligent records with clear details that your organization can use to monitor employee activity—and see anomalies. Role-based authorization and adequate due diligence checks will ensure that fraudsters can’t leverage access they aren’t supposed to have or abuse their legitimate access. As a basic protective measure, all users should have their own access—with each sign-in and event being tracked and logged. At the very least, this can be used to retroactively identify who was involved in payroll fraud—at best, it can be used to stop it in its tracks.
- The purpose of this Act is to give minimum wages to workers in the jobs listed in Schedule I of the Act, such as working in a rice mill, flour mill, or dal mill, or working in a tobacco factory, among other things.
- Ceridian’s Chief Information Security Officer explains how this type of direct deposit scam works and shares tips for identifying and preventing it.
- More Compensation Payments on top of cash with some coins scattered on top.
- This audit of expenses should uncover any claims that are inaccurate or false.
- Failing to do so not only risks substantial fines and legal action but also damages the employer’s reputation and employee morale.
Expense reimbursement fraud may be committed by padding expense, submitting fictitious expenses, or submitting expenses multiple times. A former payroll manager of a New Orleans law firm embezzled more than $2.5 million over the course of six years by paying out expense reimbursements to herself. It is interesting to note that the law firm filed a civil suit against not only the employee, but also ADP, the payroll processor, and the bank, J.P.
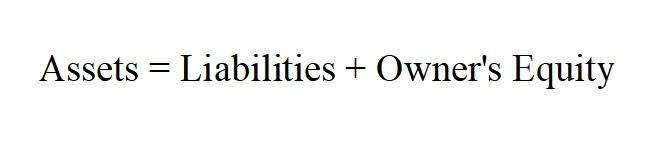
Mischaracterized expenses claims
Internal controls serve as the backbone of any organization’s efforts to prevent payroll fraud. These mechanisms are designed to create a system of checks and balances that minimize the risk of fraudulent activities. By ensuring that no single individual has control over all aspects of the payroll process, organizations can significantly reduce the likelihood of fraud. For example, the person responsible for entering payroll data should not be the same person who approves payroll disbursements. This separation of responsibilities makes it more difficult for any one person to manipulate the system for personal gain. Payroll fraud can manifest in various forms, each with its own set of tactics and implications.

